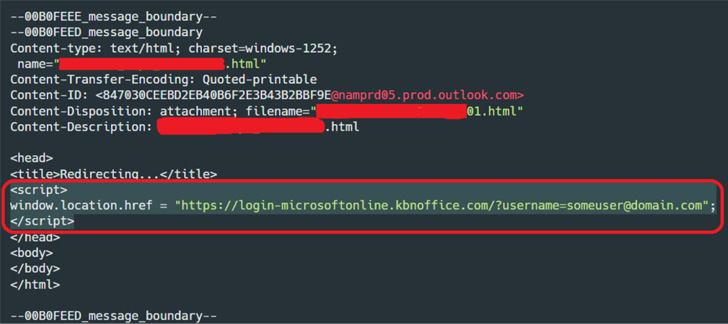
In recent months, the House of Representatives has been hard at work drafting various spending bills for the 2023 fiscal year. While these bills provide funding for a vast array of government programs and agencies, there was one thing that really stands out. Collectively, the bills that are making their way through the house allocate a staggering $15.6 billion to cybersecurity spending.
As you could probably guess, the lion’s share of this spending ($11.2 billion) is being allocated to the Department of Defense. It is worth noting, however, that nearly $3 billion is going to the Cyber Security and Infrastructure Security Agency (CISA).
Although it may be tempting to think of these cybersecurity budget allocations as just another example of excessive government spending, it’s worth considering what a $15.6 billion cash infusion will mean for the IT security industry. It’s equally important to consider why the US government finds it necessary to ramp up its cybersecurity spending to such a degree.
What Does Increased Government Cybersecurity Spending Mean for the Future?
So, what does all of this cybersecurity spending mean for the future? For starters, it means that 2023 is going to be a good year for cybersecurity companies who are authorized to sell their products to the government. Such companies will likely see record profits and may end up hiring additional staff in order to help meet the sudden demand for their products and services.
More importantly, all this spending will almost certainly drive innovation. In the past (pre-cloud), security companies would generally release a new version of their products each year to keep up with an ever-changing security landscape. These new versions almost always contained new features that were designed to entice customers and to get a leg up on competitors (who would inevitably add a comparable feature to the next version of their own product).
Although the cloud era has forced security companies to change the way that they do things, the basic concepts from years past still apply. The main difference is that the cloud has given these companies the ability to release new features and capabilities much more rapidly than might have been possible in the past.
Investing in Cybersecurity Innovation
All of this is to say that innovation has always been an important part of the cybersecurity industry. Security companies have always invested resources into developing new tools and capabilities that will help them to stay ahead of cybercriminals and competitors alike.
With billions of dollars in government spending being poured into the security industry, we will almost certainly see security products and cloud services eventually take an exponential leap forward as a direct result of being able to invest more heavily in product development and security research.
This innovation will not be limited solely to security product vendors and cloud providers. Remember that CISA is going to be receiving $2.9 billion. CISA has historically provided cybersecurity guidance and recommendations to government agencies and to the private sector.
These recommendations are not pulled from thin air but are the product of research. The increased funding will allow CISA to engage in even more cybersecurity research, ultimately positioning it to produce better recommendations.
Why is the Government Spending More on Cyber Security?
The increased budget allocations for cybersecurity are most likely tied to a White House directive from March 21, 2022 stressing the need for increased cyber defenses. This directive follows a long line of high-profile security incidents, such as last year’s attack on the Colonial Pipeline, which caused fuel shortages along the east coast.
It is worth noting that this statement was not directed exclusively at government agencies. The statement also encouraged private sector businesses to shore up their cyber security defenses in accordance with CISA guidelines.
Beef up your own cybersecurity initiatives, without the price tag
CISA offers numerous recommendations for how organizations can improve their overall cybersecurity, but many of these guidelines pertain to passwords.
If your organization isn’t quite ready to make such a hefty investment in cybersecurity, it’s a good idea to start with quantifiable metrics to see where your Active Directory is (or isn’t!) at risk. Gather your own organization-specific cybersecurity measurements with a free, read-only Password Audit from Specops.
This scan will generate reports demonstrating the effectiveness of your organization’s password policy and existing password security vulnerabilities. This free tool can also help you to identify other vulnerabilities, such as accounts that are using passwords that are known to have been leaked or passwords that do not adhere to compliance standards or industry best practices. Download the Specops Password Auditor for free today.
//e&&!t&&(jQuery.ajax({url:”https://thehackernews.com/feeds/posts/default?alt=json&max-results=4″,type:”get”,cache:!1,dataType:”jsonp”,success:function(e){for(var t=””,s=””,r=0;r
.