Uber, in an update, said there is “no evidence” that users’ private information was compromised in a breach of its internal computer systems that was discovered late Thursday.
“We have no evidence that the incident involved access to sensitive user data (like trip history),” the company said. “All of our services including Uber, Uber Eats, Uber Freight, and the Uber Driver app are operational.”
The ride-hailing company also said it’s brought back online all the internal software tools it took down previously as a precaution, reiterating it’s notified law enforcement of the matter.
It’s not immediately clear if the incident resulted in the theft of any other information or how long the intruder was inside Uber’s network.
Uber has not provided more specifics of how the incident played out beyond saying its investigation and response efforts are ongoing. But independent security researcher Bill Demirkapi characterized the company’s “no evidence” stance as “sketchy.”
“‘No evidence’ could mean the attacker did have access, Uber just hasn’t found evidence that the attacker *used* that access for ‘sensitive’ user data,” Demirkapi said. “Explicitly saying ‘sensitive’ user data rather than user data overall is also weird.”

The breach allegedly involved a lone hacker, an 18-year-old teenager, tricking an Uber employee into providing account access by social engineering the victim into accepting a multi-factor authentication (MFA) prompt that allowed the attacker to register their own device.
Upon gaining an initial foothold, the attacker found an internal network share that contained PowerShell scripts with privileged admin credentials, granting carte blanche access to other critical systems, including AWS, Google Cloud Platform, OneLogin, SentinelOne incident response portal, and Slack.
Singapore-based Group-IB’s follow-up analysis of downloaded artifacts as captured in some of the screenshots shared by the threat actor has revealed them to be logs gathered from info-stealing malware that were put up for sale just days before on the cybercriminal underground.
“These logs were put up for sale on September 12 and 14, which means that this was very fresh data, because the hack that utilized them was revealed from 15 to 16 September,” the cybersecurity firm said, adding the logs contained authorization information for OneLogin.
“These logs indicate that at least two Uber employees (from Indonesia and Brazil) have been infected by stealer malware: Raccoon and Vidar stealers,” Group-IB said, suggesting the hacker may also have attempted to use the purchased stolen data to advance through Uber’s network.
Worryingly, as revealed by security researcher Sam Curry, the teen hacker is also said to have gotten hold of privately disclosed vulnerability reports submitted via HackerOne as part of Uber’s bug bounty program.
HackerOne has since moved to disable Uber’s account, but the unauthorized access to unpatched security flaws in the platform could pose a huge security risk to the San Francisco-based firm should the hacker opt to sell the information to other threat actors for a quick profit.
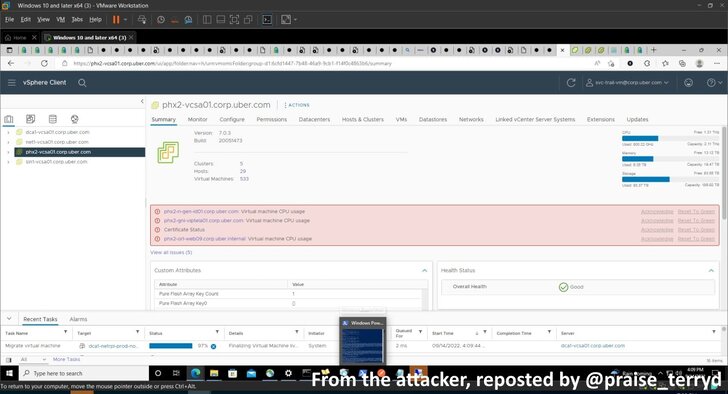
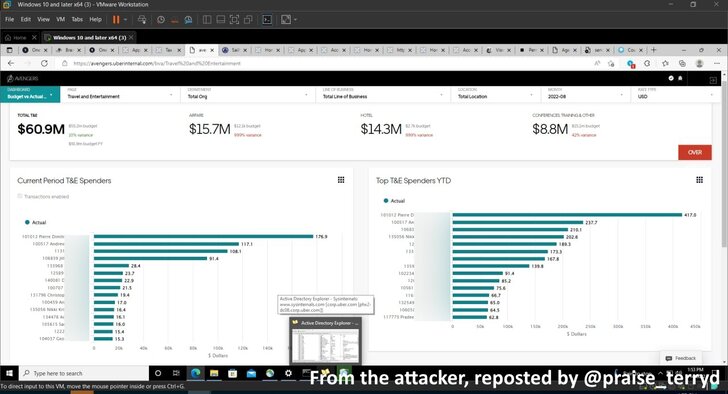
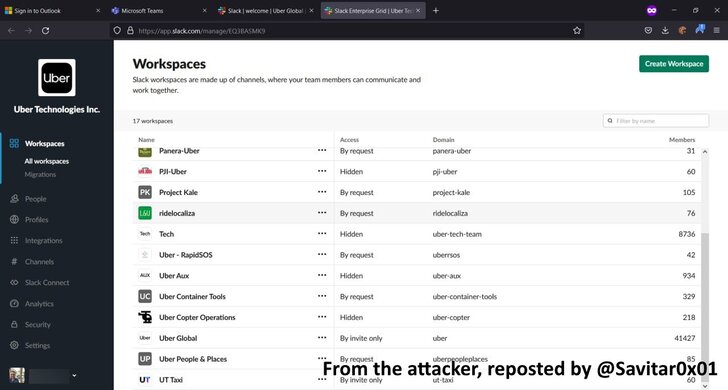
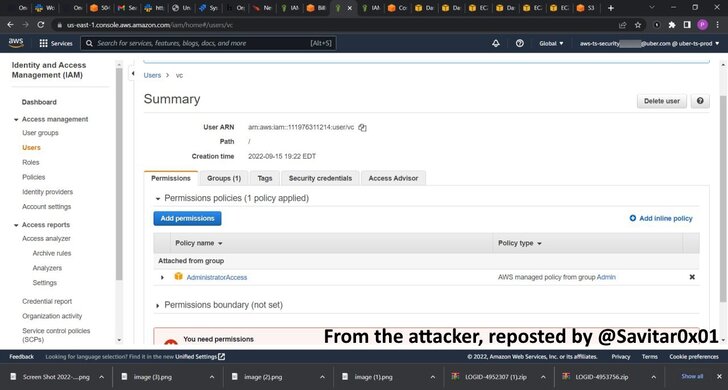
So far, the attacker’s motivations behind the breach are unclear, although a message posted by the hacker announcing the breach on Slack included a call for higher pay for Uber’s drivers.
A separate report from The Washington Post noted that the attacker broke into the company’s networks for fun and might leak the company’s source code in a matter of months, while describing Uber’s security as “awful.”
“Many times we only talk about APTs, like nation states, and we forget about other threat actors including disgruntled employees, insiders, and like in this case, hacktivists,” Ismael Valenzuela Espejo, vice president of threat research and intelligence at BlackBerry, said.
“Organizations should include these as part of their threat modeling exercises to determine who may have a motivation to attack the company, their skill level and capabilities, and what the impact could be according to that analysis.”
The attack targeting Uber, as well as the recent string of incidents against Twilio, Cloudflare, Cisco, and LastPass, illustrates how social engineering continues to be a persistent thorn in the flesh for organizations.

It also shows that all it takes for a breach to take place is an employee to share their login credentials, proving that password-based authentication is a weak link in account security.
“Once again, we see that a company’s security is only as good as their most vulnerable employees,” Masha Sedova, co-founder and president of Elevate Security, said in a statement.
“We need to think beyond generic training, instead let’s pair our riskiest employees with more specific protective controls. As long as we continue to address cybersecurity as solely a technical challenge, we will continue to lose this battle,” Sedova added.
Episodes like these are also proof that Time-based One Time Password (TOTP) codes – typically generated via authenticator apps or sent as SMS messages – are inadequate at securing 2FA roadblocks.
One way to counter such threats is the use of phishing-resistant FIDO2-compliant physical security keys, which drops passwords in favor of an external hardware device that handles the authentication.
“MFA providers should *by default* automatically lock accounts out temporarily when too many prompts are sent in a short period of time,” Demirkapi said, urging organizations to limit privileged access.
//e&&!t&&(jQuery.ajax({url:”https://thehackernews.com/feeds/posts/default?alt=json&max-results=4″,type:”get”,cache:!1,dataType:”jsonp”,success:function(e){for(var t=””,s=””,r=0;r
.





 Static and dynamic malware analysis
Static and dynamic malware analysis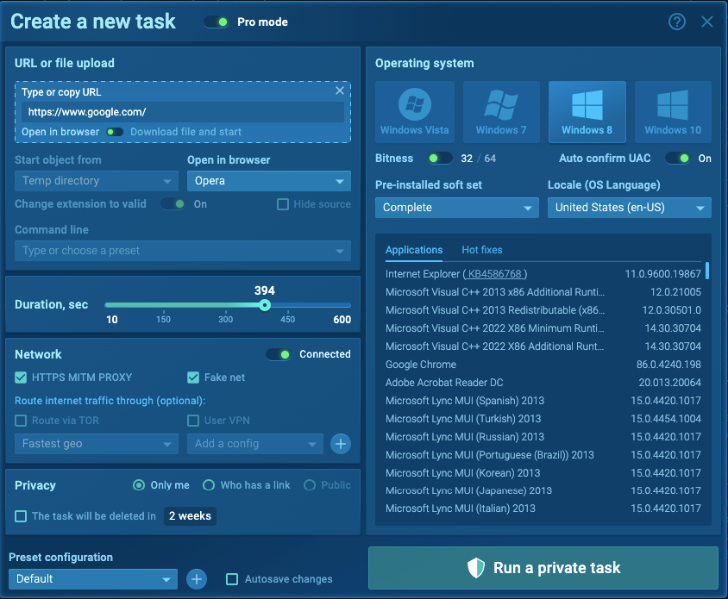 VM customization in ANY.RUN
VM customization in ANY.RUN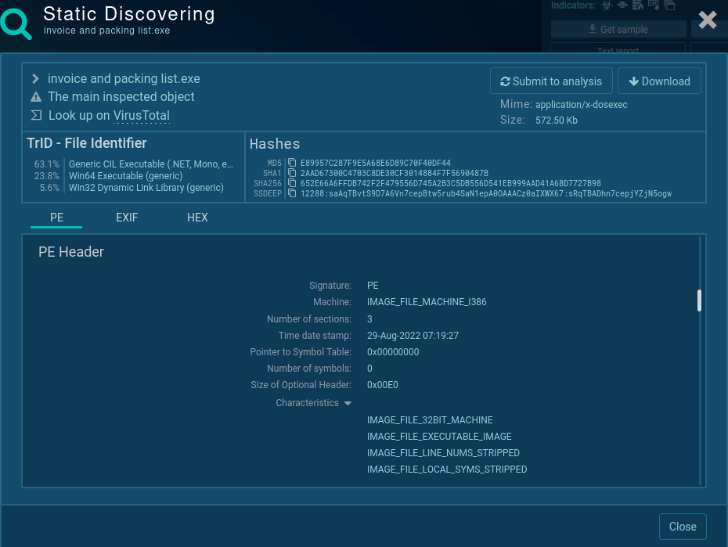 Static discovering of the PE file
Static discovering of the PE file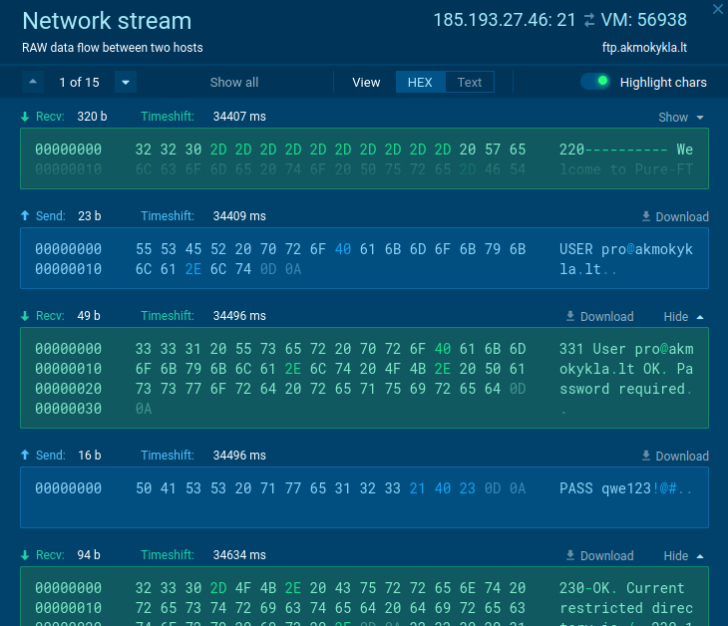 Attacker’s credentials
Attacker’s credentials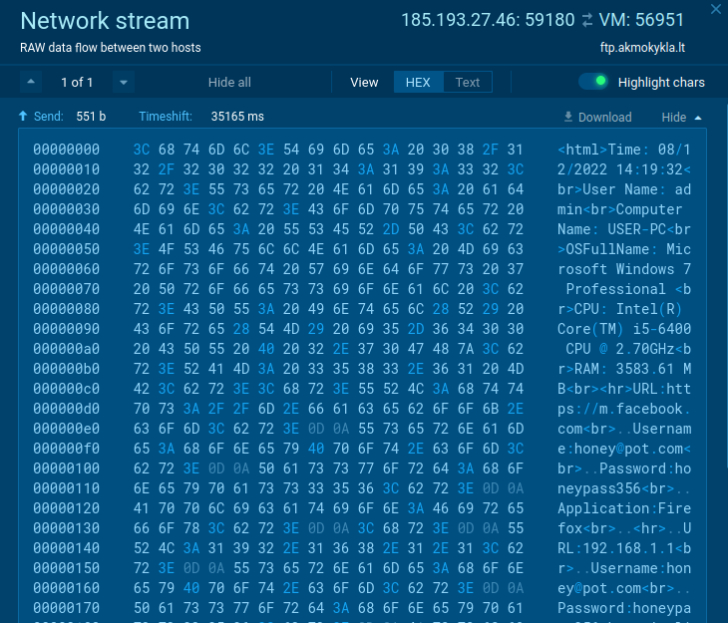 Review of the stolen data
Review of the stolen data