Understanding the connection between GRC and cybersecurity
When talking about cybersecurity, Governance, Risk, and Compliance (GRC) is often considered the least exciting part of business protection. However, its importance can’t be ignored, and this is why.
While cybersecurity focuses on the technical side of protecting systems, networks, devices, and data, GRC is the tool that will help the entire organization understand and communicate how to do it.
What does it mean?
GRC tools like StandardFusion help companies define and implement the best practices, procedures, and governance to ensure everyone understands the risks associated with their actions and how they can affect business security, compliance, and success.
In simple words, GRC is the medium for creating awareness around cybersecurity’s best practices to reduce risks and achieve business goals.
Why is cybersecurity more relevant than ever before
Cybersecurity aims to protect sensitive business data, intellectual property, personal and health information, and other company systems from cyber-attacks and threats. However, this task has become increasingly harder over the past few years.
Why is that?
Well, because of the ever-increasing global connectivity, new hybrid work models, the popularization of cloud services, and the evolution of technology, among others. Although all of these are great from a business perspective, they introduce new risks and challenges.
Here’s the truth:
Cybersecurity has always been a critical part of organizations; however, in today’s technological and interconnected landscape, they can’t exist without it, at least in the long term.

Understanding the principles of GRC
Governance, Risk, and Compliance (GRC) is a business strategy for managing a company’s overall governance, enterprise risk management, and regulatory compliance.
From a cybersecurity standpoint, GRC is a structured approach to aligning IT (people and operations) with business objectives while effectively managing risks and meeting regulatory needs.
In this context, to achieve business objectives and maximize the company’s bottom line, organizations need to follow the best practices and procedures. This is why GRC exists… to mitigate any threat to productivity and the company’s value by creating standards, policies, regulations, and processes.
More importantly, GRC helps build trust in the organization. This trust comes from improved efficiencies, better communication, employees’ confidence to share information, and enhanced business outcomes.
That’s not all.
GRC empowers companies to create a culture of value, giving everyone the education and agency to understand how they can protect the business’s value, reputation and make better decisions.
The crucial role of GRC in cybersecurity
Organizations must align people, systems, and technologies with business objectives to achieve solid and effective cybersecurity. This means everyone should know and take the proper actions when executing their tasks — it’s all about awareness and knowledge.
Governance, Risk, and Compliance is the best tool to create an integrated system that focuses on achieving objectives while addressing risks and acting with integrity.
GRC is crucial because it supports cybersecurity with vital business activities, such as:
- Standardizing the best practices for everyone to act with integrity and security.
- Assigns roles and responsibilities to business units and users, enhancing communication.
- Helping with the implementation of data manipulation procedures.
- Unifies vocabulary across departments and teams.
- Supporting internal audits and encourages continuous control monitoring.
- Assisting with risk mitigation internally and externally
- Supporting meeting industry and government regulations.
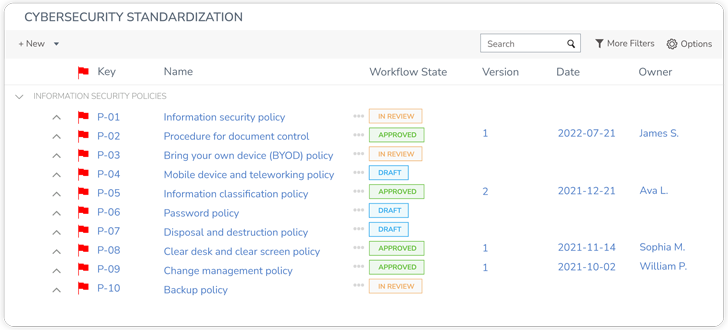
GRC also provides a framework to integrate security and privacy with the organization’s overall goals. Why is this important? Because it allows businesses to make informed decisions regarding data security risks quickly while mitigating the risk of compromising privacy.
The role of GRC in cybersecurity – technical benefits
The following are some of the vital benefits GRC offers cybersecurity:
Third-party vendor selection: Many organizations will use a third-party scorecard to gather basic information about potential vendors. This information includes: Corporate reputation, financials, network security, history of cyber breaches, geographic location, and more. A robust GRC model would support IT and security teams select and vet potential third-party vendors. More importantly, GRC will support the creation of vendor assessments and mitigation strategies.
Risk mitigation: IT can use GRC to understand the scope of cybersecurity and document the strengths and limitations of the current security program. GRC allows organizations to outline and act on different types of threats, potential damages, mitigation plans, and risk treatments.
Regulatory compliance: GRC is vital in keeping compliance in the loop as new regulations evolve worldwide. Moreover, it brings these evolving changes to the security team’s attention ahead of time, providing time to plan and respond. Overall, GRC will help develop and manage the policies, regulations, and standards to meet the often-updated business and industry regulations.
Audit support: Modern organizations extend their procedures and protocols to provide proof and audit material to their auditors. Ensuring processes and best practices are well documented will show that the house is kept in order. Critical audit material may include: Incident response, cybersecurity awareness training, internal control test results, cybersecurity compliance reviews, and more. GRC helps craft and maintain a single source of truth for compliance that allows everyone to be on the right page.
Data privacy: GRC helps organizations stay on top of the ever-changing landscape of privacy regulations. How? by allowing the IT team to ensure that the appropriate protection, logging, geographic storage, etc. are in place to defend customers’ and employees’ data.
Visibility: GRC’s integrated approach allows companies to get visibility into every aspect of their security compliance programs. This is vital as it enables different units, managers, and personnel to see the big picture and make data-drive and informed decisions.
In summary:
A well-planned GRC program enables organizations to:
- Collect and maintain high-quality information
- Improve decision making
- Promote collaboration
- Increase accountability
- Build a strong culture
- Increase efficiency and agility
- Provide visibility
- Reduces costs by supporting suitable investments
- Increase integration
- Protect the company’s value and reputation
GRC and Cybersecurity: Why do companies need an integrated approach?
Integrating GRC and cybersecurity is imperative for organizations that want to build a long-term, successful security strategy. Aside from faster communication, congruent metrics, collaboration, and decision-making, the integration of GRC and cybersecurity offers other distinct advantages.
An integrated approach minimizes manual input and the potential for human error, reducing costs and giving organizations more time to create more value for the business.
More importantly, a strong integration helps the board to clearly and comprehensively visualize the organization’s security posture. By understanding the cross-functional posture, business directors can tell better security stories to convey trust to customers and empower employees.
To sum up:
GRC and cybersecurity work hand in hand toward a lower-risk future and value creation — they can’t exist without each other. While cybersecurity aims to protect systems, networks, and data (from a technical perspective), GRC communicates the best method and practices to achieve so.
With an integrated approach, organizations will:
- Increase efficiencies
- Enhance security posture
- Tell better security stories
- Improve visibility across the board
- Increase support from leadership
- Avoid compliance/regulatory fines
- IT and security teams set the tone for the entire company
- Hand in hand toward a lower-risk future
Empowering cybersecurity through GRC – methodology
The OCEG has developed this Capability Model (Red Book) as an open-source methodology that merges the sub-disciplines of governance, risk, audit, compliance, ethics/culture, and IT into a unified approach.
Organizations can evolve this standard to address specific situations, from small projects to organization-wide rollouts. Some examples are:
- Anti-corruption projects
- Business continuity
- Third-party management
The model is key to framing conversations about GRC capabilities with the board, senior executives, and managers. Also, organizations might use this GRC Capability Model with more specific functional frameworks, such as: ISO, COSO, ISACA, IIA, NIST, and others.
The GRC Capability Model encourages organizations to document best practices to:
- Unify vocabulary across disciplines
- Define common components and elements
- Define common information requirements
- Standardize practices for things like policies and training
- Identify communication for everyone involved.
Now, let’s see how it works.
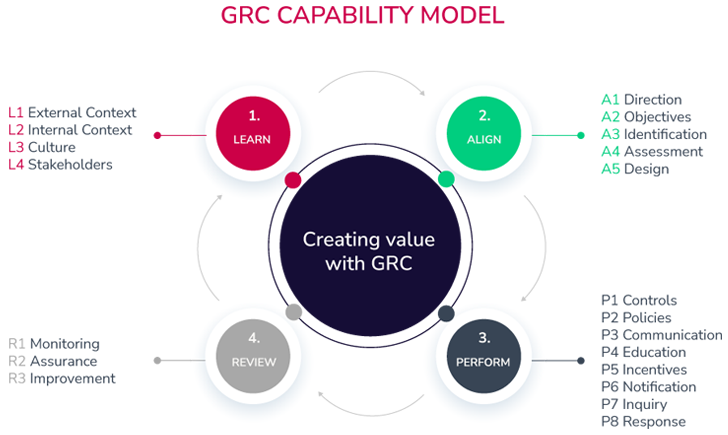
The Capability Model has four parts:
1. Learn
The main idea here is to identify the business culture, stakeholders, and organization’s business practices to successfully guide their goals, strategy, and objectives.
As a process, it would look like this:
- Learning business plans and goals
- Understanding strategic objectives
- Being aware of the current and future compliance activities
- Connecting with the key stakeholders
2. Align
This step focuses on unifying strategy with objectives and actions with strategies. The goal here is to have an integrated approach where senior leadership is engaged and supports the process of decision-making.
In simple words, this process needs:
- Align business objectives with the strategy
- Align executives with stakeholders’ expectations
- Align resource allocation planning with objectives
3. Perform
After aligning business goals and objectives, it’s time to perform. This step defines implementing appropriate controls and policies, preventing and remediating undesired risks, and monitoring to detect issues as soon as possible.
4. Review
As a final step, it’s imperative to review the design and operational performance of the current strategy and actions. More importantly, this step encourages organizations to analyze objectives to constantly enhance the integrated GRC activities.
What is the purpose of this model?
To develop a steady and integral improvement process to reach optimal performance and create value for the organization.
Get your free consultation with StandardFusion and learn how you can design an integrated GRC program to strengthen your cybersecurity and protect your organization’s value.
//e&&!t&&(jQuery.ajax({url:”https://thehackernews.com/feeds/posts/default?alt=json&max-results=4″,type:”get”,cache:!1,dataType:”jsonp”,success:function(e){for(var t=””,s=””,r=0;r
.