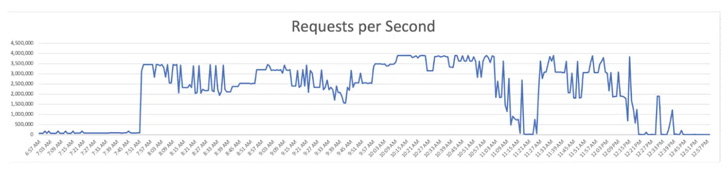
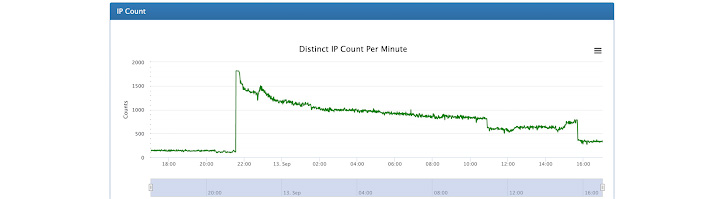
Uber on Monday disclosed more details related to the security incident that happened last week, pinning the attack on a threat actor it believes is affiliated to the notorious LAPSUS$ hacking group.
“This group typically uses similar techniques to target technology companies, and in 2022 alone has breached Microsoft, Cisco, Samsung, NVIDIA, and Okta, among others,” the San Francisco-based company said in an update.
The financially-motivated extortionist gang was dealt a huge blow in March 2022 when the City of London Police moved to arrest seven suspected LAPSUS$ gang members aged between 16 and 21. Weeks later, two of them were charged for their actions.
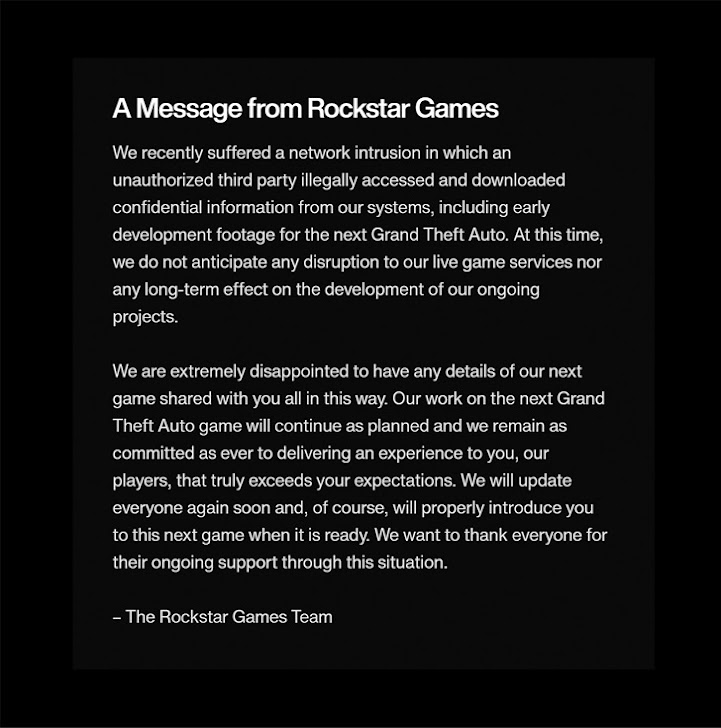
The hacker behind the Uber breach, an 18-year-old teenager who goes by the moniker Tea Pot, has also claimed responsibility for breaking into video game maker Rockstar Games over the weekend.

Uber said it’s working with “several leading digital forensics firms” as the company’s investigation into the incident continues, in addition to coordinating with the U.S. Federal Bureau of Investigation (FBI) and the Justice Department on the matter.
As for how the attack unfolded, the ridesharing firm said an “EXT contractor” had their personal device compromised with malware and their corporate account credentials stolen and sold on the dark web, corroborating an earlier report from Group-IB.
The Singapore-headquartered company, the previous week, noted that at least two of Uber’s employees located in Brazil and Indonesia were infected with Raccoon and Vidar information stealers.
“The attacker then repeatedly tried to log in to the contractor’s Uber account,” the company said. “Each time, the contractor received a two-factor login approval request, which initially blocked access. Eventually, however, the contractor accepted one, and the attacker successfully logged in.”
Upon gaining a foothold, the miscreant is said to have accessed other employee accounts, thereby equipping the malicious party with elevated permissions to “several internal systems” such as Google Workspace and Slack.
The company further said it took a number of steps as part of its incident response measures, including disabling impacted tools, rotating keys to the services, locking down codebase, and also blocking compromised employee accounts from accessing Uber systems or alternatively issuing a password reset for those accounts.
Uber didn’t disclose how many employee accounts were potentially compromised, but it reiterated that no unauthorized code changes were made and that there was no evidence the hacker had access to production systems that support its customer-facing apps.
That said, the alleged teen hacker is said to have downloaded some unspecified number of internal Slack messages and information from an in-house tool used by its finance team to manage certain invoices.
Uber also confirmed that the attacker accessed HackerOne bug reports, but noted that “any bug reports the attacker was able to access have been remediated.”
“There is only one solution to making push-based [multi-factor authentication] more resilient and that is to train your employees, who use push-based MFA, about the common types of attacks against it, how to detect those attacks, and how to mitigate and report them if they occur,” Roger Grimes, data-driven defense evangelist at KnowBe4, said in a statement.
Chris Clements, vice president of solutions architecture at Cerberus Sentinel, said it’s crucial for organizations to realize that MFA is not a “silver bullet” and that not all factors are created equal.

While there has been a shift from SMS-based authentication to an app-based approach to mitigate risks associated with SIM swapping attacks, the attack against Uber and Cisco highlights that security controls once considered infallible are being bypassed by other means.
The fact that threat actors are banking on attack paths such as adversary-in-the-middle (AiTM) proxy toolkits and MFA fatigue (aka prompt bombing) to trick an unsuspecting employee into inadvertently handing over MFA codes or authorizing an access request signals the need to adopt phishing-resistant methods.
“To prevent similar attacks, organizations should move to more secure versions of MFA approval such as number matching that minimize the risk of a user blindly approving an authentication verification prompt,” Clements said.
“The reality is that if an attacker only needs to compromise a single user to cause significant damage, sooner or later you are going to have significant damage,” Clements added, underscoring strong authentication mechanisms “should be one of many in-depth defensive controls to prevent compromise.”
//e&&!t&&(jQuery.ajax({url:”https://thehackernews.com/feeds/posts/default?alt=json&max-results=4″,type:”get”,cache:!1,dataType:”jsonp”,success:function(e){for(var t=””,s=””,r=0;r
.